Manually Configuring Office 365 for mxHERO Protection (Part 2)
Transport Rule
Table of Contents
This is Part 2 of Configuring Office 365 for mxHERO Fusion. Part 1 can be found here.
After creating the Outbound Connector, you have to set up a Transport Rule that will in fact route messages from the Office 365 environment to mxHERO.
The steps are:
- Office 365 will receive the incoming or outgoing email
- Office 365 via this transport rule will route the message to the mxHERO platform
- mxHERO will process your Mail2Cloud rules.
- If your delivery is to your own domain, mxHero will send the email back to Office 365. Office 365 will then see that the message was already processed by mxHero (using an identification header) and will deliver it to the recipient. If your delivery is to an external domain, mxHero will deliver directly to the recipient's mail server. Please see mxHERO's Improving Delivery with SPF.
If the Office 365 integration is limited to a subset of users, you will need to create two transport rules, one for incoming email and another for outgoing email. If integration is for all users then only one rule is required. In this example, we are creating two rules so that we can restrict mxHERO usage to a subset of users.
Another important point to mention is the header values displayed in these examples. These are the signatures added by mxHero. mxHero support will provide a unique, domain-specific signature to be added as the header value.
1) Create two transport rules
In your Exchange administration Office 365 dashboard, access:
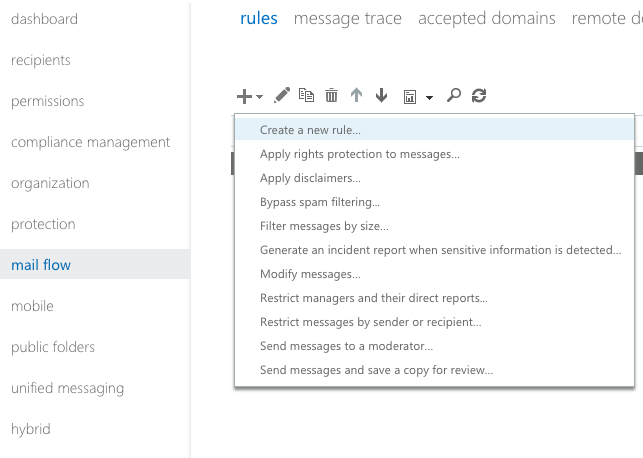
To limit mxHERO to a specific subset of users, create two rules (for senders and recipients) for a pre-defined Office 365 group. In the below example we have defined a group called, "POC".
For full integration of Office 365 and mxHERO simply create one rule with no conditional (i.e. "Apply this rule if...")
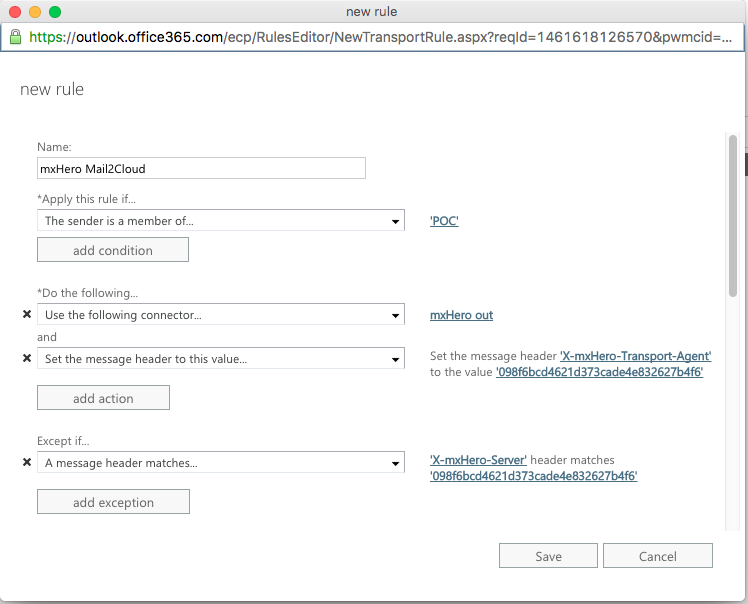
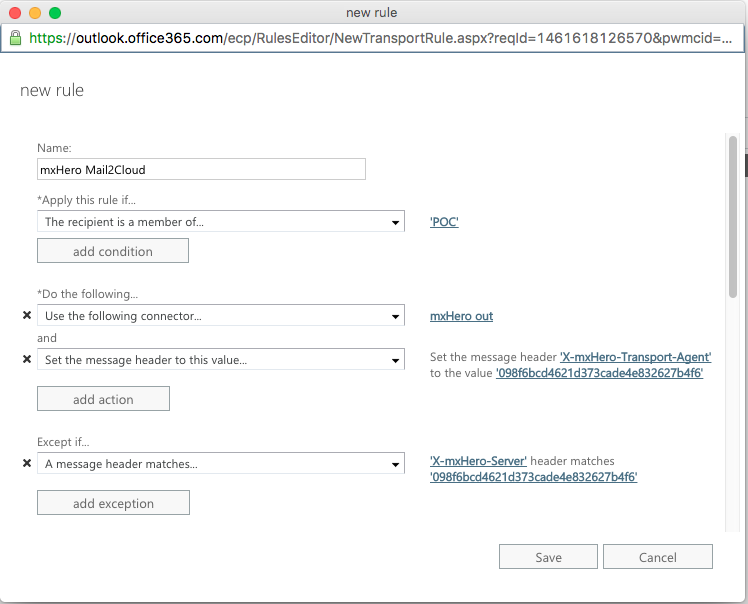
2) Whitelist mxHERO IPs
Now, let's whitelist mxHERO IPs in Exchange Online:
Go to "Protection", "Connection Filter", edit "Default" and add the following entries to the "IP Allow list":
54.208.111.28 54.236.184.32 54.165.252.128 54.165.253.193 3.211.77.148 52.22.51.97 54.209.222.83 107.23.152.206
3) Prevent TNEF encapsulation
Finally, let's prevent Office 365 to generate messages with TNEF encapsulation: